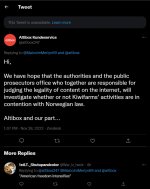
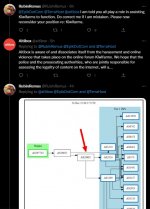
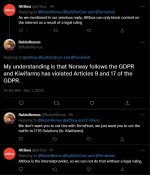
I remember @kiwifarmske was posting a lot of updates while KF was down during #DropKiwiFarms:
She eventually migrated to @kiwifarmsreview
https://twitter.com/kiwifarmsreview/with_replies
But she hasn't tweeted anything out about the new downtime. I hope she can log back into this account and start posting updates during the downtime again.
No. The purpose of Tor is to anonymize information exchange between a client and a server. Tor doesn't decentralize the client or the server themselves, but the path that the information passing through the internet takes to get from one end of the communication to the other. The Tor network itself, in other words the conglomeration of onion routers through which information requests pass from the client to a server, that is semi-decentralized. Not the .onion sites themselves:
When a website provides a .onion variant of itself like KF does, it uses Tor's hidden services to hide its location from the end user. That doesn't mean the web server itself is decentralized. The .onion variant is presumably still on a single server somewhere, perhaps even the same server as the clearnet site. Also, I know from the comments in the TG thread and during #DropKiwiFarms that a lot of Kiwis don't actually use the .onion address (because it's long and having to copy-paste it all the time is cumbersome) but merely access the clearnet site (.net) through the Tor network.
IIRC, she performed an NMAP port scan on a DNS server (IP address 193.142.147.186) and discovered that the SSH (Secure Shell) port was still listening.

There's nothing unusual about that. This is what a security minded network engineer would do while his site is under attack: shut down all other services but the most necessary ones, like SSH.
Malicious false bar complaints against one of KF's lawyers, Nick Rekieta:
Frivolous Complaints and Frivolous Complainants ...
In the Matter of the Complaints against Nicholas R. Rekieta, a Minnesota Attorney, Registration No. 0397061.
Complainants @GayestFesh @GinroDino @keffals
@Esqueer_
In this video, Nick Rekieta talks about these frivolous complaints and how @keffals and @Esqueer_ convinced frivolous complainants including @GayestFesh and @GinroDino to attack him according to baseless allegations.
She eventually migrated to @kiwifarmsreview
https://twitter.com/kiwifarmsreview/with_replies
But she hasn't tweeted anything out about the new downtime. I hope she can log back into this account and start posting updates during the downtime again.
I thought the entire point of hosting a website on the "dark web" with a .onion address was that it decentralizes access to it and so the site cannot be taken down this easily.
No. The purpose of Tor is to anonymize information exchange between a client and a server. Tor doesn't decentralize the client or the server themselves, but the path that the information passing through the internet takes to get from one end of the communication to the other. The Tor network itself, in other words the conglomeration of onion routers through which information requests pass from the client to a server, that is semi-decentralized. Not the .onion sites themselves:
Are .onion sites decentralized?
Basically - no: the way you're accessing them is decentralized, but the sites are quite centralized to the very HS server serving them.

Are .onion sites decentralized?
Blockchain technology has given rise to something called "decentralized domains" like .crypto that cannot be censored, nor rented (in the case of namebase.io), unlike DNS domains like .co...tor.stackexchange.com
When a website provides a .onion variant of itself like KF does, it uses Tor's hidden services to hide its location from the end user. That doesn't mean the web server itself is decentralized. The .onion variant is presumably still on a single server somewhere, perhaps even the same server as the clearnet site. Also, I know from the comments in the TG thread and during #DropKiwiFarms that a lot of Kiwis don't actually use the .onion address (because it's long and having to copy-paste it all the time is cumbersome) but merely access the clearnet site (.net) through the Tor network.
Elaine was saying that the KF .PHP service is still up
IIRC, she performed an NMAP port scan on a DNS server (IP address 193.142.147.186) and discovered that the SSH (Secure Shell) port was still listening.
There's nothing unusual about that. This is what a security minded network engineer would do while his site is under attack: shut down all other services but the most necessary ones, like SSH.