Well Goddamn...KF be cracking, but on some rs though, I wish more niggas realized how much Lolcowery of place KF is. I just wish people weren't too pussy made just to see for themselvesYou might have a point here I don't believe anything these fruitcakes say about themselves... ...themselves...
Incidentally I think Anominous may be Chinese as I remember him talking about his mother making red braised pork belly. Which would have been unknown outside of chinese immigrant populations until long after Anom was a kid. He even mentions several times that pork belly can be hard to find since it is mostly turned into bacon in north america making it more or less impossible to source outside of again immigrant populations with access to specialized markets back in those days. Pretty hard to imagine some white lady knowing where to get the ingredients never mind knowing how to cook it as it's a fairly complex dish.
Holy shit anom is even more cracked than I thought. He has posted about "Mao's red pork belly" dozens and dozens of times. This could however be something to throw people off the trail, even still it's nuts how much this half a faggot talks about fucking pork belly.
View attachment 57356View attachment 57357View attachment 57358
Podcast Flyer
Welcome Statement🧅
Welcome to Onionfarms. All races, ethnicities, religions. Gay, straight, bisexual. CIS or trans. It makes no difference to us. If you can rock with us, you are one of us. We are here for you and always will be.
Follow Onionfarms/Kenneth Erwin Engelhardt
Onionfarms Merchandise(Stripe Verified): Onionmart
Onionfarms.net (Our social network site powered by Humhub).Register and up your own little space to chat and hang out in.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Joshua Conner Moon - Kiwi Farms Joshua Moon Megathread
- Thread starter Randy Know
- Start date
- Featured
-
- Tags
- 1776hosting 1776hosting.com 2tsuki bear chemical cringe deceptive deviant dick fancy fancy bear farms fat flow flow chemical fraud huckster josh joshua conner moon joshua connor moon joshua moon kengle kenneth erwin engelhardt kiwi kiwifarms mental illness moon null onionfarms picture pizza stocking vincent vincent zhen warwick ri zhen
Joshua Moon the owner of Kiwifarms
KampungBoy
Local Moderator
Since the TERFs are completely protected they've been saying some wild shit too the whole site is absolutely blooming with lolcowery.Well Goddamn...KF be cracking, but on some rs though, I wish more niggas realized how much Lolcowery of place KF is. I just wish people weren't too pussy made just to see for themselves
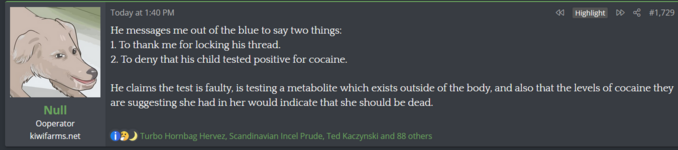
"picking mentally ill people to abuse is a very common tactic for this reason" Could almost be like how multiple mentally ill people suffered because of you, Josh
He trauma dumps fairly regularly now about having debilitating ADHD and I remember he dropped that it wasn't his dad who reined in all his spastic destructive behavior but rather his mom who sounded pretty abusive. That seems like a common asian family dynamic stereotype with tiger moms being overbearing and insensitive while the dad is more meek etc. but idk. I've always gotten a sheltered suburban WASP vibe from him but one thing's certain he's extremely fucking weird and his outbursts and use of image board slang is abnormal for a guy who's by his own admission pushing 60.You might have a point here I don't believe anything these fruitcakes say about themselves...
Incidentally I think Anominous may be Chinese as I remember him talking about his mother making red braised pork belly. Which would have been unknown outside of chinese immigrant populations until long after Anom was a kid. He even mentions several times that pork belly can be hard to find since it is mostly turned into bacon in north america making it more or less impossible to source outside of again immigrant populations with access to specialized markets back in those days. Pretty hard to imagine some white lady knowing where to get the ingredients never mind knowing how to cook it as it's a fairly complex dish.
Holy shit anom is even more cracked than I thought. He has posted about "Mao's red pork belly" dozens and dozens of times. This could however be something to throw people off the trail, even still it's nuts how much this half a faggot talks about fucking pork belly.
View attachment 57356View attachment 57357View attachment 57358
Time 4 Guillotines
Local Moderator
Some schizo shit cooked up by a Scotsman with Swiss cheese brains from Creutzfeldt-Jakob disease.What's wrong with kwiffar?
I will continue calling them Kiwi Kultists
ipreferpickles
An Onion Among Onions
The Cuck Trolly is born
Or maybe stop being a sped idk
KampungBoy
Local Moderator
Several things here....
1. This is peak NPC/modern person/terminally online weirdo shit
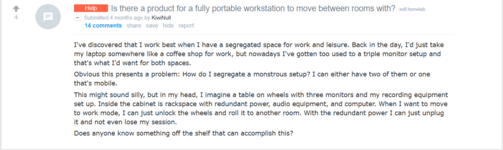
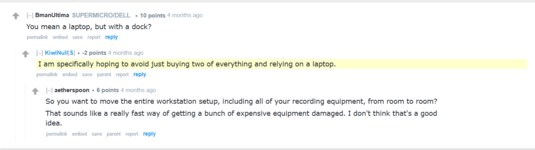
2. Null doesn't know about even basic battery backups which is kind of a must for anyone who works with a computer.
3. Null is so soft and effete he can't even attach a bunch of casters to a normal table to make it move.
4. He doesn't trust the Kiwis to have this knowledge so he has to go to........ Reddit. That's right in the case of home DIY projects Null trusts a fucking redditor over his own site members.
Null Ratched.I wonder who has based their entire life and livelihood around abusing the mentally ill

Imagine being such a lazy fuck that you sleep in until at least 8am every day, and until noon often enough to mention it and yet still whine about how hard your life is.Old Josh post but he drinks 8 litres of soda everyday.
View attachment 57393
Just put him out there with people who do actual shit out there, like y'know, children who work their entire ass off, put him out there in a place like cambodia (He'd die instantly)Imagine being such a lazy fuck that you sleep in until at least 8am every day, and until noon often enough to mention it and yet still whine about how hard your life is. ...is.
ipreferpickles
An Onion Among Onions
I need him to show proof rekieta messaged him
youthful_ shannel
An Onion Among Onions
the proof is in Joselyns panty pudding.I need him to show proof rekieta messaged him
lmao, not beating the coke & pizza allegations, eh?Old Josh post but he drinks 8 litres of soda everyday.
View attachment 57393
AshleyBloatedSwalloHole
The Official Coward of Onionfarms; Cannot Talk To A Fat Woman
An Onion Among Onions
Aka Cocaine & Child Porn.lmao, not beating the coke & pizza allegations, eh?
Maybe Josh and Rekieta should make a childAka Cocaine & Child Porn.
KampungBoy
Local Moderator
I mean on another note what does "regular sleep schedule" even mean when you have a 4 hour window of when you may or may not wake up? that's like highschoole on summer vacation sleep hours.Imagine being such a lazy fuck that you sleep in until at least 8am every day, and until noon often enough to mention it and yet still whine about how hard your life is.